New Article
LIMITED REGISTRATION
SO
ACT NOW
I-LinCP PRESENTS
1st ANNUAL MEGA MIXER
July 11, 2017
4:00 to 7:00p.m.
THE WELL
5539 UTSA Blvd.
REGISTER HERE
Participating Organizations:
I-LinCP, AIA SA, CREW SA, CCIM, IFMA SA Chapter, Construction Leadership Council, ULI SA, SMPS SA
Participating Organization Members: FREE
Non-Members: $10
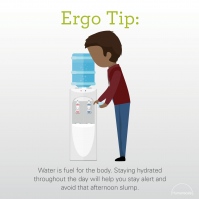
Ergo Tips
Nicole Plummer

Account Development Representative
Humanscale
San Antonio, TX 78108
Mobile 210-612-1475
Calendar of Events Import
|
New Article
 What If Your Building Automation System is Hacked?
Key Points
What If Your Building Automation System is Hacked?
Key Points
- A hack of your building automation system can threaten business operations and critical data.
- There's a 26 percent chance a breach will happen over the next 24 months.
- Develop mitigation procedures in advance to help you get safely back in operation after a hack.
A 'hack' is the unauthorized access into a computer system or network. Hacking not only threatens business operations and critical data, but it can be very costly. According to the Ponemon Institute:
- The average total cost of a data breach is $4 million.
- The average cost incurred for each lost or stolen record is $158.
- Almost half of all breaches are malicious attacks, which cost more to remediate
Your building automation system (BAS) could be the next victim of a data breach. So what do you do if you're hacked? The U.S. Department of Defense (DOD) recommends these steps:
1. Turn to previously developed mitigation procedures. This includes a pre-planned method of analysis, your response to each expected outcome and a related course of action. Assuming you prepared in advance, you'll also have the necessary tools, defined interfaces, communications channels and mechanisms in place. This prevents decisions being made in haste with unintended consequences.
2. Preserve evidence of a cyber attack for forensic analysis. Unplanned mitigation actions can very easily destroy forensic evidence. You'll want to seriously consider the impact of shutting down or disconnecting the system or making other modifications just to keep the system operational
3. Compare existing versus baseline operational conditions of network entry points. This includes firewalls, routers, wireless access points and remote-access terminals. It also includes network topology, network traffic and machine/device configurations. Determine if an unusual Internet protocol (IP) address or an unusual port, protocol or service (from a known IP address) is attempting to communicate with the BAS.
4. Systematically recover each affected device. Preferably, you'll want to remove and replace affected devices with off-the-shelf replacements. The second best option is to re-image affected devices. All devices in the network should be re-flashed (overwrite the memory) with reliable software to provide confidence that re-infection won't occur.
5. Systematically reintegrate devices, processes and network segments. Once individual devices in a functional group have been tested, reintegrate these groups and, finally, reintegrate the network layers
6. Routinely monitor devices to make sure they're not re-infected. Compare expected normal BAS activity to observed BAS activity to search for differences. Map each routine monitoring task to the individuals most likely to perform the check.
For more information, see the DOD's Advanced Cyber Industrial Control System Tactics, Techniques, and Procedures.
Be prepared. There's a 26 percent chance a breach will happen over the next 24 months. Develop mitigation procedures ahead of time and you'll be safely back in operation much faster.
CSUSA Business Matters has been prepared solely for the purpose of providing helpful information to users of this service. The information has been compiled by Questline, a contractor to Comfort Systems USA; however, no representation is made by either Questline or Comfort Systems USA as to the completeness or accuracy of the information contained therein. In particular, some information may be incomplete, may contain errors or may be out of date. In addition, neither Questline nor Comfort Systems USA endorses any product or service mentioned therein.

Stephanie Rainbow, FMP, CFM, SFP
Business Development Manager
MTech
(210) 319-9363 Cell |